逆向攻防世界CTF系列38-xxxorrr
逆向攻防世界CTF系列38-xxxorrr
64位无壳,很自然的找到main和一个比较函数
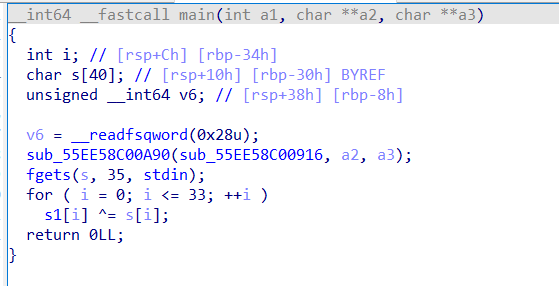
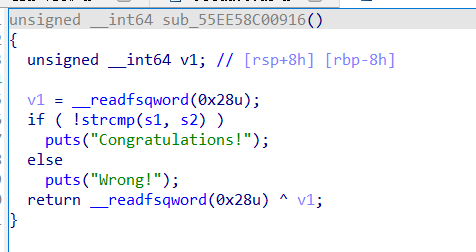
以为逻辑很简单了
enc = [
0x56, 0x4E, 0x57, 0x58, 0x51, 0x51, 0x09, 0x46, 0x17, 0x46,
0x54, 0x5A, 0x59, 0x59, 0x1F, 0x48, 0x32, 0x5B, 0x6B, 0x7C,
0x75, 0x6E, 0x7E, 0x6E, 0x2F, 0x77, 0x4F, 0x7A, 0x71, 0x43,
0x2B, 0x26, 0x89, 0xFE
]
key = [
0x71, 0x61, 0x73, 0x78, 0x63, 0x79, 0x74, 0x67, 0x73, 0x61,
0x73, 0x78, 0x63, 0x76, 0x72, 0x65, 0x66, 0x67, 0x68, 0x6E,
0x72, 0x66, 0x67, 0x68, 0x6E, 0x6A, 0x65, 0x64, 0x66, 0x67,
0x62, 0x68, 0x6E, 0x00
]
for i in range(len(enc)):
print(chr((enc[i] ^ key[i]) % 256),end='')
'/$ 2(}!d''“:/m-T<A*$INçþ
一堆乱码,看看有什么不对,发现s1的交叉引用居然有4个
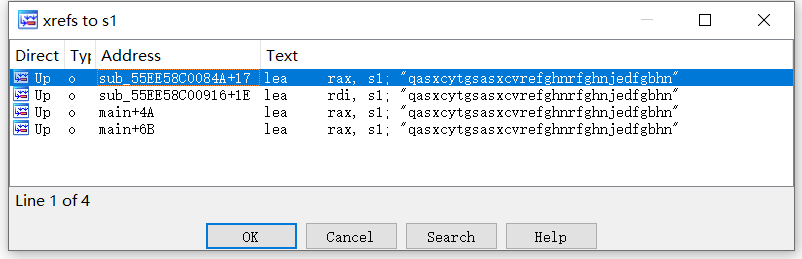
找到了这个
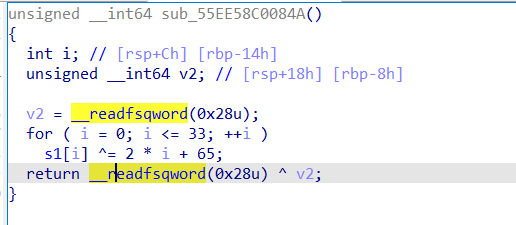
再对这个函数进行交叉引用定位到
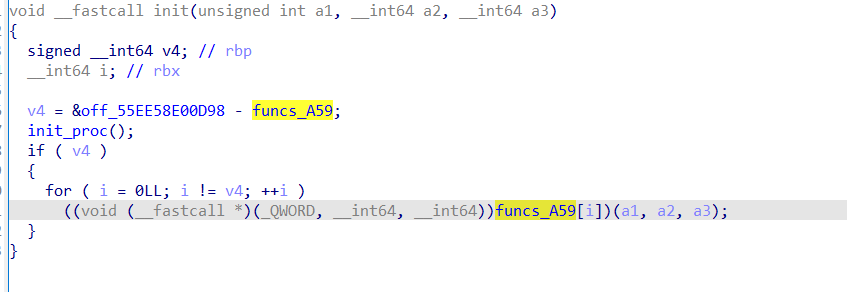
应该是做了一个初始化,改了S1的值,可以动态调试验证一下,这里我对s1下了个硬件断点,发现s1确实改变了
写解密代码:
enc = [
0x56, 0x4E, 0x57, 0x58, 0x51, 0x51, 0x09, 0x46, 0x17, 0x46,
0x54, 0x5A, 0x59, 0x59, 0x1F, 0x48, 0x32, 0x5B, 0x6B, 0x7C,
0x75, 0x6E, 0x7E, 0x6E, 0x2F, 0x77, 0x4F, 0x7A, 0x71, 0x43,
0x2B, 0x26, 0x89, 0xFE
]
key = [
0x71, 0x61, 0x73, 0x78, 0x63, 0x79, 0x74, 0x67, 0x73, 0x61,
0x73, 0x78, 0x63, 0x76, 0x72, 0x65, 0x66, 0x67, 0x68, 0x6E,
0x72, 0x66, 0x67, 0x68, 0x6E, 0x6A, 0x65, 0x64, 0x66, 0x67,
0x62, 0x68, 0x6E, 0x00
]
for i in range(len(enc)):
print(chr((enc[i] ^ (2 * i + 65)^ key[i]) % 256),end='')
flag{c0n5truct0r5_functi0n_in_41f}
- 感谢你赐予我前进的力量
赞赏者名单
因为你们的支持让我意识到写文章的价值🙏
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 Matriy
评论
匿名评论
隐私政策
你无需删除空行,直接评论以获取最佳展示效果