逆向攻防世界CTF系列59-reverse-for-the-holy-grail-350
逆向攻防世界CTF系列59-reverse-for-the-holy-grail-350
64位,无壳
int __fastcall main(int argc, const char **argv, const char **envp)
{
int valid; // ebx
int v4; // ebx
__int64 v5; // rbx
void *v7[2]; // [rsp+0h] [rbp-70h] BYREF
_BYTE v8[16]; // [rsp+10h] [rbp-60h] BYREF
void *v9[2]; // [rsp+20h] [rbp-50h] BYREF
_BYTE v10[16]; // [rsp+30h] [rbp-40h] BYREF
void *v11[2]; // [rsp+40h] [rbp-30h] BYREF
char v12[24]; // [rsp+50h] [rbp-20h] BYREF
v11[0] = v12;
v11[1] = 0LL;
v12[0] = 0;
std::__ostream_insert<char,std::char_traits<char>>(&std::cout, "What... is your name?", 21LL);
std::endl<char,std::char_traits<char>>(&std::cout);
std::operator>><char>(&std::cin, v11);
std::__ostream_insert<char,std::char_traits<char>>(&std::cout, "What... is your quest?", 22LL);
std::endl<char,std::char_traits<char>>(&std::cout);
std::istream::ignore((std::istream *)&std::cin);
std::getline<char,std::char_traits<char>,std::allocator<char>>(&std::cin, v11);
std::__ostream_insert<char,std::char_traits<char>>(&std::cout, "What... is the secret password?", 32LL);
std::endl<char,std::char_traits<char>>(&std::cout);
std::operator>><char>(&std::cin, &userIn[abi:cxx11]);
v7[0] = v8;
std::string::_M_construct<char *>(v7, userIn[abi:cxx11], qword_601AE8 + userIn[abi:cxx11]);
valid = validChars(v7);
if ( v7[0] != v8 )
operator delete(v7[0]);
if ( valid < 0 )
goto LABEL_8;
v9[0] = v10;
std::string::_M_construct<char *>(v9, userIn[abi:cxx11], qword_601AE8 + userIn[abi:cxx11]);
v4 = stringMod(v9);
if ( v9[0] != v10 )
operator delete(v9[0]);
if ( v4 < 0 )
{
LABEL_8:
std::__ostream_insert<char,std::char_traits<char>>(&std::cout, "Auuuuuuuugh", 11LL);
std::endl<char,std::char_traits<char>>(&std::cout);
}
else
{
std::__ostream_insert<char,std::char_traits<char>>(&std::cout, "Go on. Off you go. tuctf{", 25LL);
v5 = std::__ostream_insert<char,std::char_traits<char>>(&std::cout, userIn[abi:cxx11], qword_601AE8);
std::__ostream_insert<char,std::char_traits<char>>(v5, "}", 1LL);
std::endl<char,std::char_traits<char>>(v5);
}
if ( v11[0] != v12 )
operator delete(v11[0]);
return 0;
}
反编译后非常的乱,但是直接看到了Go on,,,,tuctf{},我们往前看看,看到关键v4,v4由stringMod产生,跟进
__int64 __fastcall stringMod(__int64 *a1){
int v14[18]; // [rsp+0h] [rbp-60h] BYREF
memset(v14, 0, sizeof(v14));
v1 = a1[1];
if ( v1 ){
v2 = *a1;
v3 = 0LL;
v4 = 0;
do{
v12 = *(char *)(v2 + v3);
v14[v3] = v12;
if ( 3 * ((unsigned int)v3 / 3) == (_DWORD)v3 && v12 != firstchar[(unsigned int)v3 / 3] ) v4 = -1;
++v3;
}
while ( v3 != v1 );
}
else{
v4 = 0;
}
v5 = v14;
v6 = v14;
v7 = 666;
do{
*v6 = v7 ^ *(unsigned __int8 *)v6;
v7 += v7 % 5;
++v6;
}
while ( &v15 != (__int64 *)v6 );
v8 = 1;
v9 = 0;
v10 = 1;
v11 = 0;
do{
if ( v11 == 2 ){
if ( *v5 != thirdchar[v9] ) v4 = -1;
if ( v10 % *v5 != masterArray[v9] ) v4 = -1;
++v9;
v10 = 1;
v11 = 0;
}
else {
v10 *= *v5;
if ( ++v11 == 3 ) v11 = 0;
}
++v8;
++v5;
}
while ( v8 != 19 );
return (unsigned int)(v7 * v4);
}
简单看一遍,v4不能为0和-1否则返回肯定<=0
这里肯定是校验,我们再返回主函数仔细看看,理一理
void *v11[2]; // 存储用户名
std::__ostream_insert<char,std::char_traits<char>>(&std::cout, "What... is your name?", 21LL);
std::endl<char,std::char_traits<char>>(&std::cout);
std::operator>><char>(&std::cin, v11);//输入用户名
//输入quest
std::__ostream_insert<char,std::char_traits<char>>(&std::cout, "What... is your quest?", 22LL);
std::endl<char,std::char_traits<char>>(&std::cout);
std::istream::ignore((std::istream *)&std::cin);
std::getline<char,std::char_traits<char>,std::allocator<char>>(&std::cin, v11);
//输入密码
std::__ostream_insert<char,std::char_traits<char>>(&std::cout, "What... is the secret password?", 32LL);
std::endl<char,std::char_traits<char>>(&std::cout);
std::operator>><char>(&std::cin, &userIn[abi:cxx11]);
std::string::_M_construct<char *>(v7, userIn[abi:cxx11], qword_601AE8 + userIn[abi:cxx11]);
// 校验密码,不是重点
valid = validChars(v7);
关键还得看StringMod
第一部分:
do
{
v12 = *(char *)(v2 + v3);
v14[v3] = v12;
if (3 * ((unsigned int)v3 / 3) == (_DWORD)v3 && v12 != firstchar[(unsigned int)v3 / 3])
v4 = -1;
++v3;
}
while (v3 != v1);
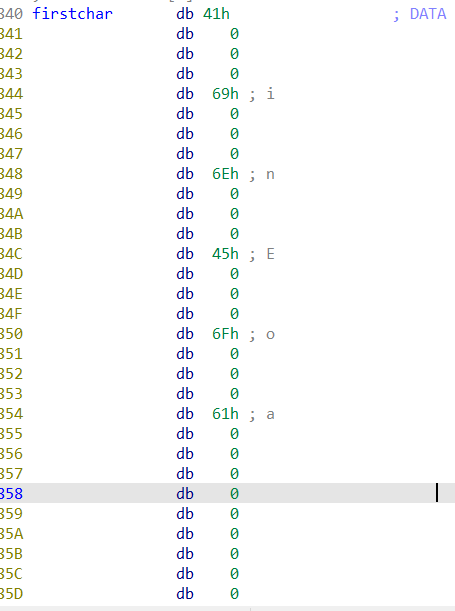
3 * ((unsigned int)v3 / 3) == (_DWORD)v3表示v3是3的倍数,并且v12一定要为firstchar[v3/3],因为v4不能为-1
一开始firstchar第一个是41h dd要改成跟下面db一样
第二部分:
int v7 = 666;
do
{
*v6 = v7 ^ *(unsigned __int8 *)v6;
v7 += v7 % 5;
++v6;
}
while (&v15 != (__int64 *)v6);
遍历
v14中的每个元素,使用 XOR 加密*v6 = v7 ^ *v6。v7不断通过v7 += v7 % 5更新,变化的方式和v6的变化不容易看出具体的模式,但本质是一个简单的加密操作。
第三部分:
v8 = 1;
v9 = 0;
v10 = 1;
v11 = 0;
do{
if (v11 == 2) {
if (*v5 != thirdchar[v9])
v4 = -1;
if (v10 % *v5 != masterArray[v9])
v4 = -1;
++v9;
v10 = 1;
v11 = 0;
}
else
{
v10 *= *v5;
if (++v11 == 3)
v11 = 0;
}
++v8;
++v5;
}
while (v8 != 19);
v8初始值是1不能=19,说明长度为18
其实简单模拟下就知道++v11 == 3条件肯定不会满足,二,每三次满足v11 == 2,比如v5的第2,5,8….位
怎么比对呢?靠v9,1,2,3,4,5…..那么下面其实需要改成dd(按d)
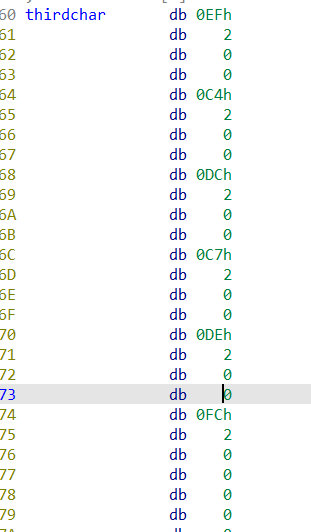
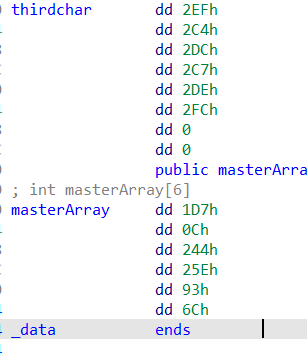
这里不能直接shift+e获取,写脚本吧
idc.get_wide_byte(addr),从虚拟地址addr处读取一个字节值
idc.get_wide_word(addr),从虚拟地址addr处读取一个字(2字节)值
idc.get_wide_dword(addr),从虚拟地址addr处读取一个双字(4字节)值
idc.get_qword(addr),从虚拟地址addr处读取一个四字(8字节)值
ida_bytes.patch_byte(addr,byte),设置虚拟地址addr处的一个字节值
ida_bytes.patch_word(addr,word),设置虚拟地址addr处的一个字值
ida bytes.patch_dword(addr,dword),设置虚拟地址addr处的一个双字值
ida_bytes.patch_qword(addr,qword),设置虚拟地址addr处的一个四字值如果addr包含有效数据,则返回1,否则返回0
ida bytes.is loaded(addr)
db:db定义字节类型变量,一个字节数据占1个字节单元,读完一个,偏移量加1
dw:dw定义字类型变量,一个字数据占2个字节单元,读完一个,偏移量加2
dd:dd定义双字类型变量,一个双字数据占4个字节单元,读完一个,偏移量加4
start_addr = 0x601840
res = []
for i in range(0,24,4):
res.append(idc.get_wide_word(start_addr + i))
print(res)
# [65, 105, 110, 69, 111, 97]
# [751, 708, 732, 711, 734, 764]
# [471, 12, 580, 606, 147, 108]
写解密脚本:
key1 = [65, 105, 110, 69, 111, 97]
key2 = [751, 708, 732, 711, 734, 764]
key3 = [471, 12, 580, 606, 147, 108]
flag = [0 for i in range(18)]
j = 0
for i in range(0,18,3):
flag[i] = key1[j]
j += 1
v7=666
xor = []
for i in range(18):
xor.append(v7)
v7 += v7%5
index2 = 0
for i in range(2,18,3):
flag[i] = key2[index2] ^ xor[i]
index2 += 1
index3 = 0
for i in range(1, 18, 3):
for a in range(32, 128, 1):
if ((flag[i - 1] ^ xor[i - 1]) * (a ^ xor[i])) % (flag[i + 1] ^ xor[i + 1]) == key3[index3]:
flag[i] = a
index3 += 1
break
print('tuctf{' + ''.join(map(chr, flag)) + '}')
好难
参考:攻防世界逆向高手题之reverse-for-the-holy-grail-350_攻防世界 reverse-for-the-holy-grail-350-CSDN博客
- 感谢你赐予我前进的力量