逆向攻防世界CTF系列31-elrond32
逆向攻防世界CTF系列31-elrond32
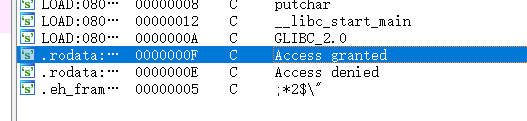
追踪
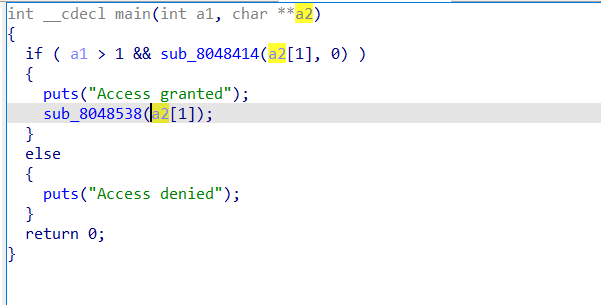
跟进sub_8048538
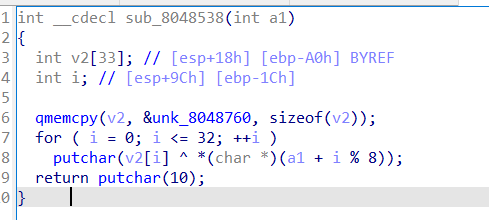
这是输出
回头看sub_8048414
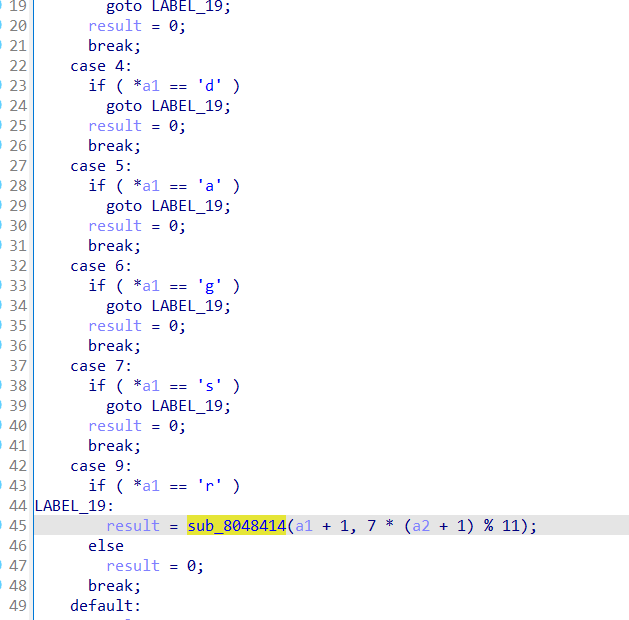
可以发现是个递归,模拟一下得到字符串a2(main中的是a2,这里代表a1)是isengard
取出密文,idapython代码
start_addr = 0x08048760
end_addr = 0x080487E3
list = []
for i in range(start_addr,end_addr,4):
list.append(idaapi.get_dword(i))
print(list)
# [15, 31, 4, 9, 28, 18, 66, 9, 12, 68, 13, 7, 9, 6, 45, 55, 89, 30, 0, 89, 15, 8, 28, 35, 54, 7, 85, 2, 12, 8, 65, 10, 20]
解密代码:
enc = [15, 31, 4, 9, 28, 18, 66, 9, 12, 68, 13, 7, 9, 6, 45, 55, 89, 30, 0, 89, 15, 8, 28, 35, 54, 7, 85, 2, 12, 8, 65, 10, 20]
key = 'isengard'
for j in range(33):
print(chr(enc[j] ^ ord(key[j % 8])),end='')
flag{s0me7hing_S0me7hinG_t0lki3n}
- 感谢你赐予我前进的力量
赞赏者名单
因为你们的支持让我意识到写文章的价值🙏
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 Matriy
评论
匿名评论
隐私政策
你无需删除空行,直接评论以获取最佳展示效果